Cybersecurity with Ed Adams
May 13, 2019
Ed Adams is the President & CEO of Security Innovation. Ed has presented to tens of thousands of security professionals at reputable industry events such as RSA Conference (US and Asia), Ponemon Institute’s RIM Renaissance, Connected Security Expo, Mozilla’s Privacy Lab. Ed is a Ponemon Institute Research Fellow, Privacy by Design Ambassador by the Information & Privacy Commissioner of Canada, and Forbes Technology Council Member. He sits on the board of The International Consortium of Minority Cyber Professionals (ICMCP) and is a BoSTEM Advisory Committee member.
What are your thoughts on the current global cybersecurity threats?
For many people (i.e., non-IT professionals or those with limited IT knowledge), the word ‘cybersecurity’ is associated with websites and hackers. However, this is an overly- simplistic view because, in reality, cybersecurity risks are now much more prevalent with IOT (Internet of Things) devices, including, for example, Connected Cars.
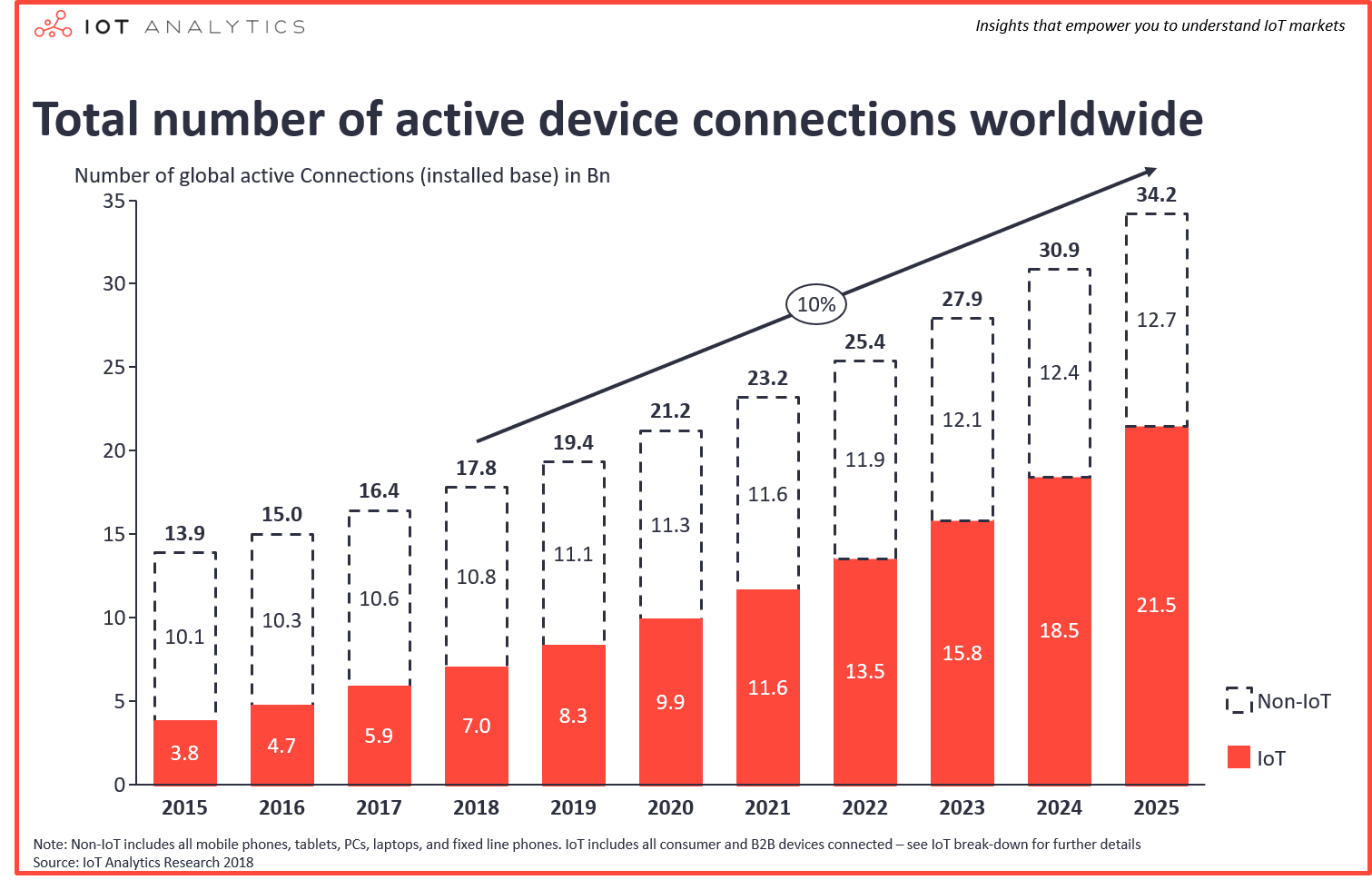
According IOT Analytics’ ‘State of the IOT and short term outlook 2018’ report, there are now over 7 billion IoT devices across the globe and a total of 17 billion connected devices – a number that is predicted to grow at an even faster pace into the future – which will invariably result in increased cybersecurity risk for businesses and individuals alike.
There are several reasons why IOT devices are particularly vulnerable to cybersecurity threats:
1. Because the software is often not designed with security in mind, they automatically become an obvious and easy target for hackers looking to access confidential data quickly, without having to break through networks and secure firewalls.
2. Since the IOT is a relatively new technology that’s less than 10 years old, there is still a certain immaturity in the software development of these devices; in other words, software engineers are either not fully aware of the security risk element, or they simply don’t have the skills or knowledge to write the software securely.
3. All too often functionality and convenience trump security: security is often seen as a hindrance or an ‘optional extra’ – as opposed to a fundamental feature that enhances the user’s experience of whatever device they happen to be using.
4. While more mature industries, such as online banking and e-commerce, for example, have been influenced by government and industry regulation, IOT is still an emerging technology which has, to date, outpaced regulation and regulatory authorities.
In the case of connected cars, for example, Taylor Armerding’s Forbes article on the issue of connected cars and security, shows the staggering extent of computer control in today’s cars:
“a Dreamliner jet has about 6.5 million lines of code, while a Ford pickup has about 130 million. That truck also has about 100 different chips, more than two miles of cable and ten operating systems”.
Finally, according to the Ponemon Research Institute, 63% of manufacturers test less than half of the technologies in your car for vulnerabilities, only 33% train developers on secure coding methods, and only 10% have a dedicated cybersecurity team.
There is a shortage of cybersecurity professionals globally, how is the industry responding?
The cybersecurity industry needs to address the skills shortage as a matter of urgency: there will be 3.5 million unfilled cybersecurity jobs globally by 2021.
Some organisations have already begun to respond to this situation by training existing developers and staff to transition to cybersecurity.
Also, Artificial intelligence (AI) offers a lot of potential in terms of assisting with this skills shortage; for example, it can provide automatic responses to cybersecurity issues.

